Internet Censorship Update: Transparent DNS Proxy Implemented by Malaysian ISPs on Cloudflare and Google Public DNS Servers
6th August 2024, Transparent DNS proxy redirecting DNS queries to Google and Cloudflare public DNS has been implemented by two Malaysian ISPs Maxis and Time, leading to users now unable to access websites officially blocked by MCMC through alternative DNS servers.
Initial findings
It was detected through automated and manual testing on 5th August, that transparent DNS proxy redirecting DNS queries to Google and Cloudflare public DNS servers has been implemented by two Malaysian ISPs Maxis and Time. Users that have configured their Internet settings to use alternative DNS servers, would have found that they are now unable to access websites officially blocked by MCMC and getting a connection timeout error.
Summary:
- On Maxis, DNS queries to Google Public DNS (8.8.8.8) servers on ip address are being automatically redirected to Maxis ISP DNS Servers; and
- On Time, DNS queries to both Google Public DNS (8.8.8.8) and Cloudflare Public DNS (1.1.1.1) are being automatically redirected to Time ISP DNS servers.
Instead of the intended Google and Cloudflare servers, users are being served results from ISP DNS servers. In addition to MCMC blocked websites, other addresses returned from ISP DNS servers can also differ from those returned by Google and Cloudflare.
Securing DNS services
Users being redirected to unauthenticated websites and services that are different from that intended can pose a security risk and result in unexpected technical issues. Standard DNS queries are also unencrypted and addresses requested by users can be viewed and logged.
Users that are affected, can configure their browser settings to enable DNS over HTTPS to secure their DNS lookups by using direct encrypted connection to private or public trusted DNS servers. This will also bypass transparent DNS proxy interference and provide warning of interference.
Firefox Web Browser
Users using Firefox web browser and enable DNS over HTTPS via Settings and the Privacy & Security Tab. Enable Max Protection to use DNS over HTTPs when browning all sites.
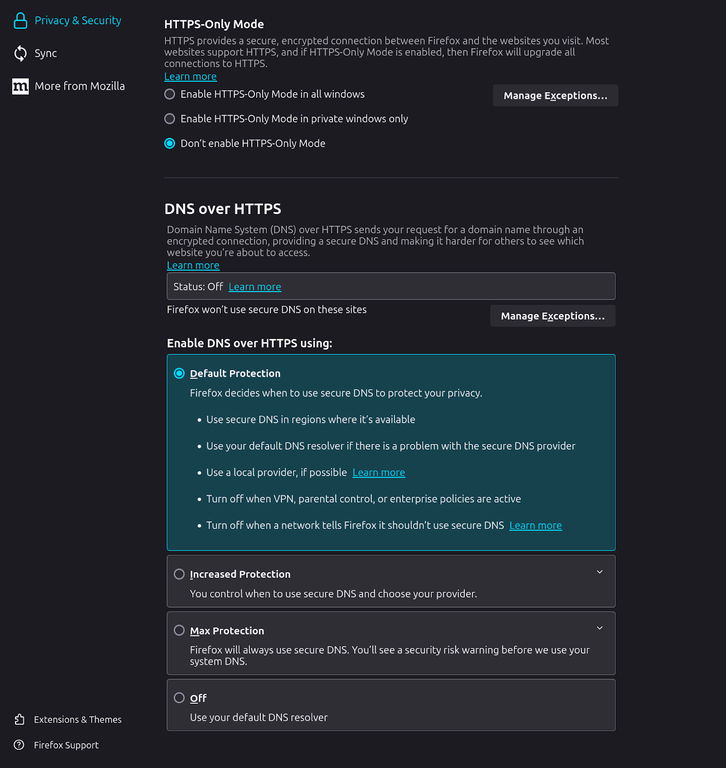
Firefox Browser Security Settings for DNS over HTTPS
Chrome Web Browser
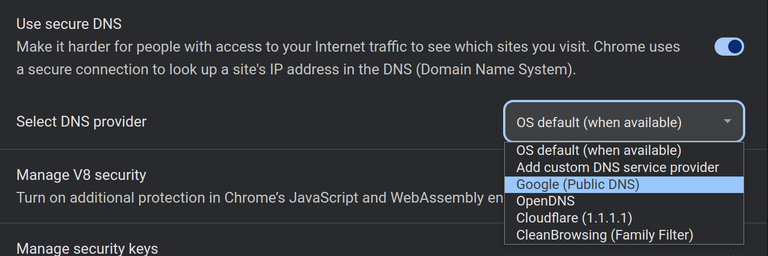
Users using Chrome Web Browser can enable DNS over HTTPS via Settings and the Security tab. Enable Use secure DNS and then select one of the public DNS servers such as Google or Cloudflare.
DNS Query and OONI network interference data
|
Domain |
ISPs implementing DNS proxy |
Datetime |
Detailed data from OONI |
|---|---|---|---|
|
www.grindr.com |
|
5 August 2024 |
OONI Explorer Link (Time/Google) OONI Explorer Link (Maxis/Cloudflare) |
|
murrayhunter.substack.com |
|
6 August 2024 |
See DNS query results. |
DNS Query Results
|
1.1.1.1 on Time (AS9930) Result: Transparent proxy DNS being implemented |
dig @1.1.1.1 murrayhunter.substack.com ; <<>> DiG 9.18.28-0ubuntu0.22.04.1-Ubuntu <<>> @1.1.1.1 murrayhunter.substack.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19278 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;murrayhunter.substack.com. IN A ;; ANSWER SECTION: murrayhunter.substack.com. 5 IN CNAME mcmc.time.net.my. mcmc.time.net.my. 924 IN A 175.139.142.25 ;; Query time: 39 msec ;; SERVER: 1.1.1.1#53(1.1.1.1) (UDP) ;; WHEN: Tue Aug 06 10:46:29 +08 2024 ;; MSG SIZE rcvd: 100 |
|
8.8.8.8 on Time (AS9930) Result: Transparent proxy DNS being implemented |
dig @8.8.8.8 murrayhunter.substack.com ; <<>> DiG 9.18.28-0ubuntu0.22.04.1-Ubuntu <<>> @8.8.8.8 murrayhunter.substack.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51496 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;murrayhunter.substack.com. IN A ;; ANSWER SECTION: murrayhunter.substack.com. 5 IN CNAME mcmc.time.net.my. mcmc.time.net.my. 938 IN A 175.139.142.25 ;; Query time: 31 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) (UDP) ;; WHEN: Tue Aug 06 10:46:16 +08 2024 ;; MSG SIZE rcvd: 100 |
|
1.1.1.1 on Maxis (AS9534) Result: Transparent proxy DNS not being implemented |
dig @1.1.1.1 murrayhunter.substack.com ; <<>> DiG 9.18.28-0ubuntu0.22.04.1-Ubuntu <<>> @1.1.1.1 murrayhunter.substack.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48122 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;murrayhunter.substack.com. IN A ;; ANSWER SECTION: murrayhunter.substack.com. 300 IN A 104.18.10.223 murrayhunter.substack.com. 300 IN A 104.18.11.223 ;; Query time: 71 msec ;; SERVER: 1.1.1.1#53(1.1.1.1) (UDP) ;; WHEN: Tue Aug 06 10:51:04 +08 2024 ;; MSG SIZE rcvd: 86 |
|
8.8.8.8 on Maxis (AS9534) Result: Transparent proxy DNS being implemented |
dig @8.8.8.8 murrayhunter.substack.com ; <<>> DiG 9.18.28-0ubuntu0.22.04.1-Ubuntu <<>> @8.8.8.8 murrayhunter.substack.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58398 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: Message has 11 extra bytes at end ;; QUESTION SECTION: ;murrayhunter.substack.com. IN A ;; ANSWER SECTION: murrayhunter.substack.com. 1800 IN CNAME mcmc-redirect.maxis.com.my. mcmc-redirect.maxis.com.my. 18 IN A 175.139.142.25 ;; ADDITIONAL SECTION: rpz.blacklist.maxis.com.my. 1 IN SOA dnsb01.men.maxis.com.my. root.rpz.blacklist.maxis.com.my. 2024130081 3600 600 1209600 3600 ;; Query time: 67 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) (UDP) ;; WHEN: Tue Aug 06 10:51:01 +08 2024 ;; MSG SIZE rcvd: 200 |
These test measurements from OONI and DNS query results confirmed that a few Malaysian ISPs (internet service providers) were implementing a transparent DNS proxy that redirects DNS queries to Cloudflare and Google DNS servers, and these ISP servers are transparently returning MCMC block server address instead of those served by Google and Cloudflare.
The data on OONI was collected through the OONI Probe App by Sinar Project and various volunteers. A confirmed blocking on OONI shows that there has been DNS blocking on the website whereby the DNS had been tampered to redirect to MCMC’s IP address: 175.139.142.25. For this case, the DNS service serving these blocked IP addresses are erroneously shown as those from Google or Cloudflare due to transparent DNS proxy being implemented by ISPs.
Call for testing
Sinar Project is calling for volunteers to help with the continuous monitoring and testing of internet censorship. Further information can be found here or our Telegram group.
For monitoring this particular implementation of Transparent DNS Proxies by ISPs in Malaysia, we encourage our volunteers to configure their DNS to 8.8.8.8 or 1.1.1.1 prior to OONI testing.
